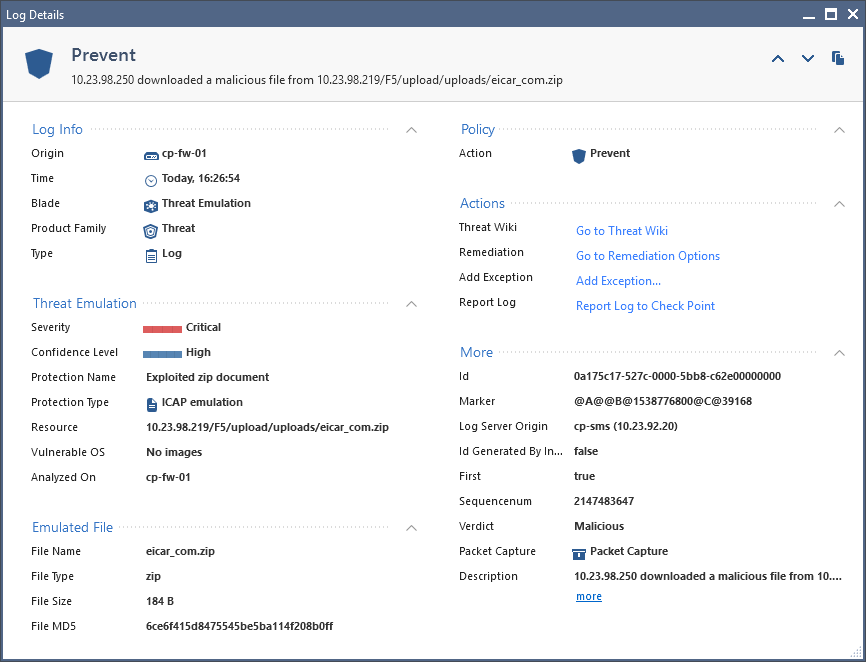
Amazon.com : JWM 20PCS TM1990A-F5 iButton Guard Tour Checkpoints Tags with Holder for iButton Patrol Wand Reader : Electronics
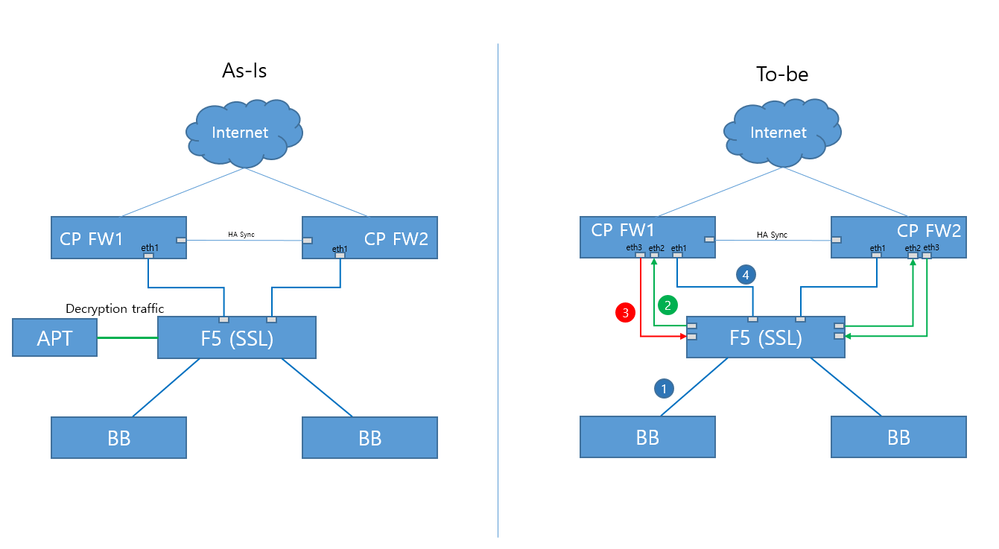
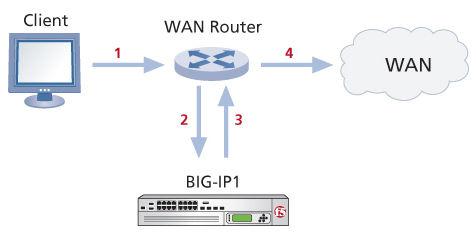
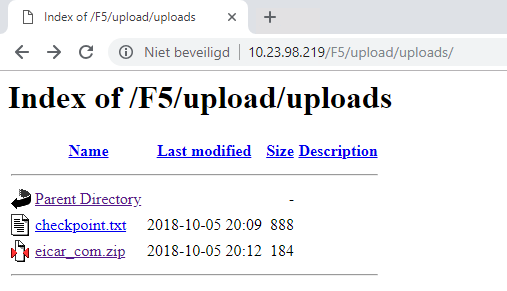
GitHub - nvansluis/f5.checkpoint_sandblast_icap: iApp template to integrate F5 BIG-IP with Check Point SandBlast ICAP server
Identification of immunologic subtype and prognosis of GBM based on TNFSF14 and immune checkpoint gene expression profiling - Figure f5 | Aging