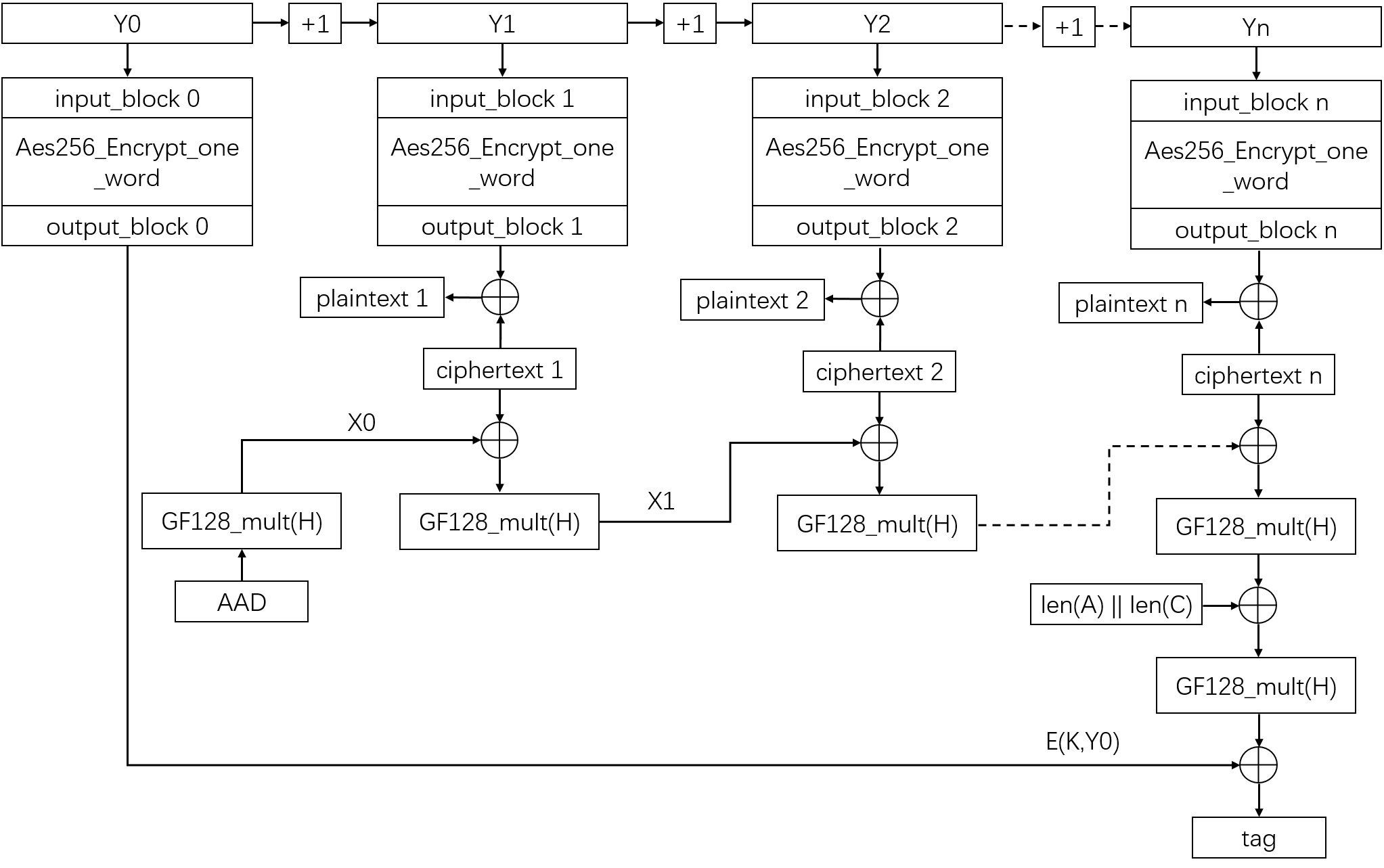
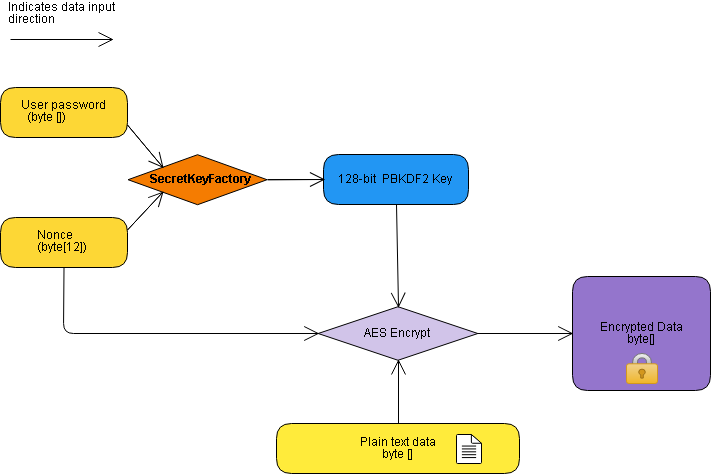
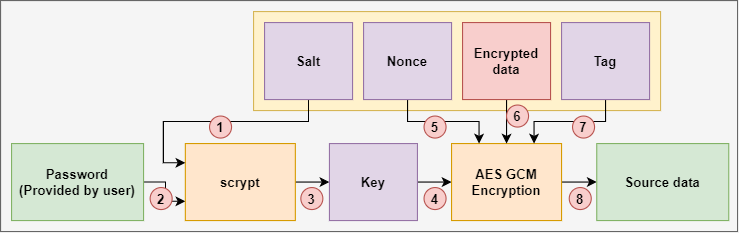
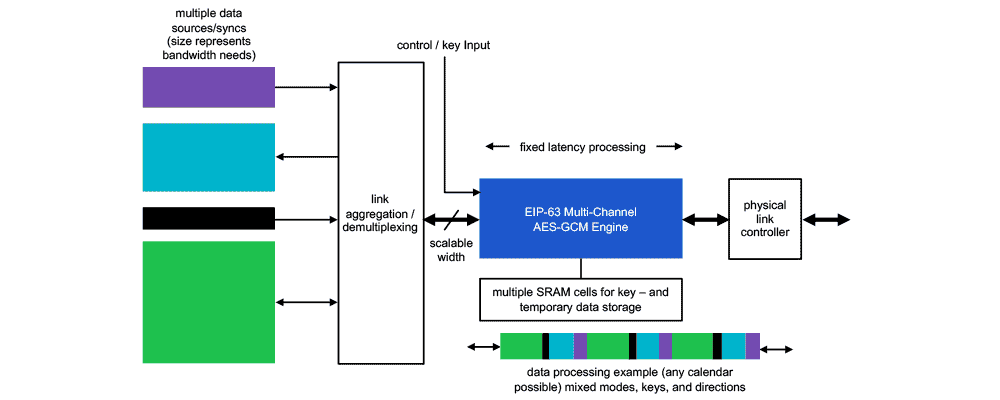
Implementation of AES-GCM encryption algorithm for high performance and low power architecture Using FPGA | Semantic Scholar

hmac - AES-GCM cipher tag and IV size, while attempting to render encrypted ciphertext useless by removing them - Cryptography Stack Exchange

Implementation of AES-GCM encryption algorithm for high performance and low power architecture Using FPGA | Semantic Scholar